What drives a privacy zealot? What does their zealotry accomplish? Are they pathological, or are we?
Bonus: submit a tiny tech review for Reboot’s inaugural end-of-year community roundup.
🎭 Threat Model
By Hal Triedman
It’s hard nowadays to disappear in America.
In the twenty-first century, basic needs1—a place to sleep, a legal address, a way to spend money, a phone, identification cards, internet accounts and a connection to access them with—cast a digital shadow. Every change of address, new bank card, phone, ID photo, IP address, and credential is logged, indexed, associated with other data points, and made searchable before being posted for sale.
The infrastructure and algorithms that enact this process are incredibly powerful. They’re the pulsating economic heart of surveillance capitalism: information flows to and from data centers like the blood of a living organism. The sheer magnitude of it can induce a sense of informational fatalism.
It’s hard to disappear, but some people try. Many of them are driven by a sense of necessity. On today’s internet, anyone can become the main character of Twitter. No one wants to be doxxed, threatened, extorted, or blackmailed with their online information—an outcome likelier for those with marginalized gender identities, sexualities, or political beliefs. For these people, seeking privacy is a reaction, a scramble to snatch back the details of one’s life before stalkers or other ill-willed strangers claim those details for their own gain.
Others are driven by curiosity about how invisible they can get. This small community of tech-savvy zealots for “extreme privacy” (a sort of internet privacy parallel of preppers) are obsessed with the challenge of privacy for its own sake. Their lives are one long blue team exercise: They use open source, security- and privacy-focused operating systems like Tails and GrapheneOS instead of Apple, Google, or Microsoft offerings; email with ProtonMail instead of Gmail; text with Signal instead of iMessage, SMS, and Facebook; search with DuckDuckGo instead of Google or Bing; browse with Tor or Brave instead of Chrome. They self-host ad-blocking Raspberry Pis and VPNs and password managers (to limit the effects of hacks of centralized password managers), and turn on hardware-based multi-factor authentication for every account, and make payments with anonymous virtual debit cards. Some go so far as to use private mailboxes, register as South Dakota “nomads” to hide their address, or form anonymous Wyoming LLCs to own property. But even if obscuring yourself is your full-time job, you will almost certainly be findable, eventually, by someone with enough resources.
Piece by piece, members of this community work to erase their presence from the public world. It’s an act of either self-annihilation or self-liberation; I can’t quite tell which.
Extreme privacy adherents show that it is possible to exist (mostly) outside of the web surveillance capitalism weaves, even though it can often be inconvenient, and costly, and taxing on your mental health. Piece by piece, members of this community work to erase their presence from the public world. It’s an act of either self-annihilation or self-liberation; I can’t quite tell which.
Is it individually pathological to go to such great lengths to disappear? Or, given what we as a society know about the invasiveness of surveillance on the modern internet, is it pathological that the rest of us don’t seem to care?
Michael Bazzell and his not-so-merry men
I can’t tell you much about Michael Bazzell. I don’t know what he looks like, or where he lives, or much about his qualifications and career history, other than the fact that he worked in law enforcement at some point in the early 2000s. His offices in Los Angeles refused multiple requests for an interview. I don’t even know if Michael Bazzell is his real name.
What I do know, however, is that Bazzell is one of the intellectual leaders of the extreme privacy community. Since 2009, he has run Intel Techniques, a website dedicated to all things privacy and OSINT. He has written four editions of Extreme Privacy (a heavy, 517-page tome written on 8.5 x 11 inch paper) and ten editions of OSINT Techniques (a volume of similar weight). Both are authoritative texts, and are often assigned in college and law enforcement courses. To date, he’s created more than 300 episodes of the Privacy, Security, and OSINT Show (he has podcast dude voice) and edited five issues of UNREDACTED Magazine, which showcases voices from within the community. He also, most importantly, runs a consultancy to help willing clients disappear. He’s a master at constructing new lives that his clients can move into and inhabit with anonymous ease, replete with private new devices, houses, cars, and bank accounts. He is, paradoxically, the most famous extreme privacy advocate.
Bazzell has clients of all genders. After all, women and queer people are disproportionately subject to intimate partner violence (IPV) that requires reactive privacy (e.g. revenge porn, sextortion, intimate deepfakes, stalkerware). For the people who face direct threat—the journalists engaged in politically sensitive work; the activists speaking truth to power; the women, trans, and nonbinary people subject to doxxing and IPV—violations of privacy are not intellectual abstractions to be mitigated. They’re tangible and concrete and can drive you out of your home.
On the other hand, the hobbyist community that has formed around extreme privacy is male-dominated, with a distinctly Web 1.0 flavor of techno-libertarianism. Throughout these documents (and the Reddit communities inspired by them) are constant references to people who don’t understand the threat model: girlfriends and wives who don’t understand why the family needs to use temporary credit cards, incredulous children who need to be dragged out of the Google ecosystem, parents who refuse to download Signal. In the world of extreme privacy, there’s a preference for individualistic direct action—namely, for the “man of the house” to use technology to protect the privacy of his family.
These people come to the practice for a wide variety of reasons. Some are predisposed toward privacy from a young age. “I kinda stumbled into hiding from the internet,” says Jonathan (not his real name), an extreme privacy practitioner who has taken the rare step of talking about his experience on Bazzell’s podcast. “At the time, I was in middle and high school.” Others advocate for privacy as a way of opening up room for personal experimentation. Oyzark (another pseudonym), for example, is a writer who is a member of both the extreme privacy community and the furry community. They advocate for anonymity to help answer the question: “How do we develop our fursonas in a way that is authentic and fun while protecting our privacy and staying safe?” Still others (like “Eugene Debs” writing from Wisconsin, “Digitally Semi-Anonymous” writing from… somewhere in the US, and “AnoninTJ” writing from Tijuana) instrumentalize privacy as a way of creating unsurveilled spaces in their lives.
Extreme privacy can be exhausting and isolating. This isolation can spread if practitioners aren’t careful. “We talk a lot about extreme privacy,” says Bazzell in a podcast episode about this phenomenon. “We don't talk about how it impacts other people in our lives… I strive to make sure that my weird dumb ways of doing all this stuff don’t eliminate my family bonds.” Oyzark, in an Unredacted piece about the successes and failures of implementing privacy in their family, asserts that extreme privacy requires self-isolation, lest it become disruptive. “Keep your privacy hobby compartmentalized. Don't try to drag your unwilling family into your extreme privacy escapades!”
Ultimately, what keeps privacy extremophiles captivated by what is, in reality, a mostly intellectual game is the submerged threat (and perhaps even the desire) that it suddenly could become much more real.
There’s also an undercurrent of paranoia that pervades the world of extreme privacy, a tension that exists in the space between necessity and curiosity. For extreme privacy adherents, every piece of true information is a potential threat. For some people, those threats have become actualized into real harm. For others, they’re a deadly virus trapped perpetually in ice. At any point, the climate can change, the ice can melt, and the virus can wreak havoc.
The psychological stakes of privacy often greatly exceed the actual level of threat these hobbyists face, and can sometimes veer into a sort of emotional cosplay. “As a privacy hobbyist, I am constantly imagining advanced threat models,” Oyzark writes. “I am fortunate that I am not being hunted down by a violent ex-spouse, I am not a journalist or whistleblower, and I am not trying to flee a repressive country. But I love imagining what I would do if I were, and trying out the technologies I would use in various extreme scenarios.”
These imaginings—these horrifying and alluring “what ifs?”—exert a pull on privacy practitioners like moths to a flame. What if someone starts stalking me? What if my political ideology becomes criminalized? What if my identity becomes criminalized? What if I win the lottery and need to lay low for a while? Does my threat model account for that? Ultimately, what keeps privacy extremophiles captivated by what is, in reality, a mostly intellectual game is the submerged threat (and perhaps even the desire) that it suddenly could become much more real.
An internet that is necessary, but not safe
Like Jonathan, I can’t exactly remember when privacy became one of my fixations. PATRIOT Act mass surveillance was pervasive throughout my childhood, and my burgeoning adolescent interest in technology dovetailed with the Snowden revelations. When they learned I was going to anti-Trump protests in 2017, my parents told me to “be careful what you post online”—after all, you never know when a government will change its stance on free expression. And there is an alluring power in invisibility: of inhabiting a view from nowhere; of being able to surveil and act upon the world without, in turn, being surveilled or acted upon by it.
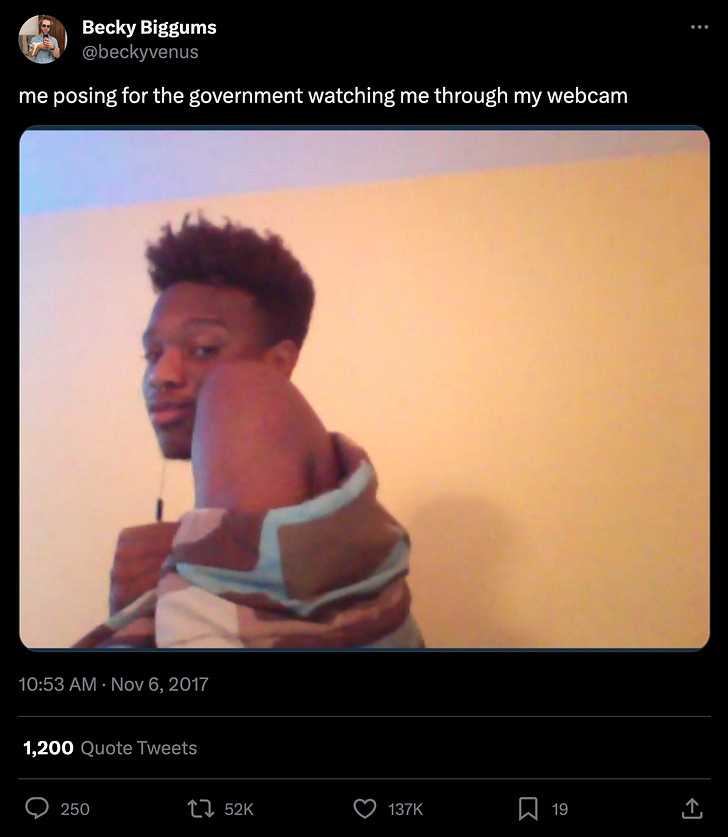
As a denizen of the internet, nearly everything you do is observed (and saved, and made searchable). The asymmetry of government mass surveillance has been common knowledge for decades: there’s an entire genre of memes dedicated to the FBI agent watching you through your webcam. As an individual, successfully defending your informational sovereignty is almost impossible, because you (and your friends, family, and broader network) always need to be perfect. A well-resourced and motivated adversary only needs to find one person who has made one mistake.
The sense of anonymity and freedom the internet gave me died slowly as I came into adulthood. I realized that the nature of the “public squares” on Twitter, Facebook, and Instagram was qualitatively different from those in real life. Unlike the immersive ambiguity of the protests I was attending, online crowds are atomic—every user has an IP address and email that can be disambiguated and isolated, photos that can be tracked and identified. In the “public” of these online forums, I felt bared and identified.
The fundamental question posed in the pursuit of privacy is the following: Do others have access to information about me that could hurt me, now or in the future?
By 2018, my internet felt necessary, but not safe—and I tried my best to close the windows and lock the doors to my digital life. At the time, I was working in progressive politics, so I followed the DNC’s personal cybersecurity checklist: I turned my social media to private and mostly stopped posting; I started using a password manager with unique, random 25+ character passwords for all my accounts and a hardware security key for multi-factor authentication; I encrypted all my devices and turned off biometric unlocking. I found Michael Bazzell’s Data Removal Guide and started manually submitting data removal requests for myself and my family; I downloaded Consumer Report’s Permission Slip app and authorized it to legally request that data brokers delete my information. These facts likely put me in the 99th percentile for privacy and security among internet users. But it never felt like enough. And knowing what I know now, it isn’t enough.
The fundamental question posed in the pursuit of privacy is the following: Do others have access to information about me that could hurt me, now or in the future? At any given point in time, this question has a verifiable answer. But no matter the answer, the psychological drive to privacy—the desire for safety, toward not feeling violated—is ultimately insatiable. To live in community is to observe and to be observed, to share space with those who could hurt you. There will always be another moment where the answer to the question of privacy could change.
The politics of privacy
In the writer’s note to Attack Surface, a book about the moral hazards of surveillance technology, author and activist Cory Doctorow writes:
Technology is a tool for social change because it can temporarily shield you from the all-seeing eye of a corrupt state… And what you need to do during that temporary, technologically-dependent window is reform your society so the government is just and responsive and transparent. Technology cannot substitute for a just society, but it can help you create that society.
Extreme privacy practitioners substitute the genuine political potential of changing surveillance capitalism—the fleeting promise of an un-enshittified internet that respects free expression and data sovereignty—with pure individualism. The paradox is that its practitioners recognize their own structural disempowerment more clearly than almost anyone else. They feel a deep, psychological need for control over their data. They run into the walls of what is technically and logistically and administratively possible every single day.
This reality points to the key misunderstanding of extreme privacy, at least in its hobby form: it posits that surveillance is an atomic problem that should be tackled by enlightened individuals or families, rather than a networked phenomenon that implicates society more broadly. The world—particularly those of us who believe in protest, political advocacy, and active participatory citizenship—undoubtedly has many practical skills to learn from extreme privacy. But as extreme privacy practitioners hide from the internet, they betray a worldview that can be just as pathological as the informational fatalism that impedes individual action on privacy: a deep nihilism about other humans.
Rendering yourself disappeared is inherently self-limiting, and invisibility is an individualistic trap. To disappear is to cede the space you once took up, to cast away the chance that, just maybe, your visibility could create change.
Hal Triedman is a contributing editor to Reboot, and a senior privacy engineer at the Wikimedia Foundation. Recently he’s been thinking about how to vanish in a puff of smoke.
Reboot publishes essays on tech, humanity, and power every week. If you want to keep up with the community, subscribe below ️⚡️
🌀 microdoses
Some of the privacy and security tools linked in this essay that I’ve found useful: DNC Personal Cybersecurity Checklist | Privacy Party | Permission Slip App | KeepassXC | Intel Techniques
Adi Robertson takes us on a deep dive into the strange history of people search sites in The Verge.
About those people search sites: McKenzie Funk has a fascinating NYT profile of Hank Asher, the Florida-based former drug smuggler and businessman who laid the foundation for the modern surveillance capitalist internet.
I got this book rec from TikTok (not great on the whole privacy front, I know, but intermittently-released dopamine is a hell of a drug ¯\_(ツ)_/¯), and it was a super fun surveillance- and privacy-focused thriller: Going Zero by Anthony McCarten
Beat this game and then use it as your password manager pass phrase
💝 closing note
We’re now accepting community submissions for Reboot’s 2023 roundup: a collection of tiny reviews reflecting the best and worst of the tech ecosystem this year.
Good tech criticism has the power to challenge, educate, and inspire; to celebrate the under-celebrated and de-hype the overhyped. To that end, we’re looking for 50-300 word commentaries on your favorite and least favorite tech products, policies, and pieces from this year. The more creative, the better—we’ll select a group to publish in the newsletter in December.
Get the full details and submit your review here by Sunday, November 26.
Thank you for reading! Have fun disappearing into thin air 🥷
Hal & the Reboot team
Of course, many people go without their basic needs, particularly those who are aggressively surveilled by police and other state apparatuses. For example: hundreds of thousands of people in the US are houseless; over 4.5 million US households lacked a bank account in 2021; and an estimated 11 million immigrants lack legal documentation, many of whom are legally prevented from getting identification.


